In recent advancements, the Gootloader malware has significantly evolved its methodologies, rendering it a sophisticated threat to organizations. Initially recognized for employing SEO poisoning to entice victims to compromised WordPress sites, Gootloader functions as a gateway for the introduction of secondary malware such as Cobalt Strike, IcedID, and SystemBC. A newly identified variant, detected in late 2023, has unveiled the "GootBot," a tailored bot that facilitates lateral movement within corporate infrastructures, enhancing the malware's ability to bypass conventional detection mechanisms more efficiently. This enhancement allows attackers to disseminate quickly throughout networks while connecting to multiple hardcoded command-and-control (C2) servers, further complicating detection initiatives.
Moreover, the malware capitalizes on seemingly legitimate business-related queries, enticing users into downloading malicious files from compromised WordPress sites. This progression is consistent with Gootloader's historical pattern of targeting diverse industries and signifies a transition towards ransomware integration, indicating an increased risk for data exfiltration and network infiltration.
Cybersecurity professionals advocate for the adoption of strategies such as activating script block logging, scrutinizing anomalies in scheduled tasks, and analyzing network traffic for any dubious activity. These approaches can facilitate the early detection of the malware’s presence and mitigate its effects prior to the deployment of additional payloads throughout the network.
Gootloader's Targeting Strategy
Gootloader has progressed remarkably from its inception as a basic malware loader to a sophisticated, multifunctional threat with extensive implications. Initially, Gootloader functioned primarily as a conventional “dropper” for various malware types, acting as an entry point to enable the deployment of multiple malicious payloads such as ransomware or spyware. Its core purpose was to establish preliminary access within a targeted infrastructure and subsequently “drop” supplementary malware components engineered to execute functions such as credential harvesting, network exploration, and lateral migration. Nevertheless, recent years have witnessed Gootloader's advancement in both complexity and purpose, transforming into a highly targeted malware instrument that has adjusted to the evolving cybersecurity environment.
One of the most alarming facets of this transformation is Gootloader’s enhanced capacity to conduct lateral movement across networks, bypass advanced security measures, and avoid detection. This evolution can be primarily attributed to the integration of the new GootBot component. Introduced in late 2023, GootBot has broadened Gootloader’s capabilities beyond its original infection purpose, enabling it to propagate within a network while maintaining a discreet operational profile. The incorporation of GootBot further highlights the malware's dependence on encrypted PowerShell scripts and other sophisticated coding methodologies, complicating detection and eradication efforts. This shift in Gootloader's methodology emphasizes the necessity of proactive defense strategies and advanced detection protocols, particularly within corporate settings.
Why WordPress Sites Are Prime Targets
A critical element in Gootloader’s recent strategic shift is the calculated targeting of WordPress sites. As the leading content management system globally, WordPress powers over 43% of websites, inherently enhancing its attractiveness to cyber criminals. The widespread adoption of the platform among both small enterprises and large organizations indicates that a successful breach of WordPress sites could significantly affect a broad and varied user base.

From a technical standpoint, WordPress’s ecosystem of themes and plugins, while essential for its personalization, also introduces considerable security vulnerabilities. Each plugin incorporated into a WordPress site presents a potential risk. Popular plugins, frequently developed by third parties and maintained with inconsistent diligence, can contain security weaknesses that Gootloader and other malicious actors can exploit. For instance, plugins with unresolved SQL injection vulnerabilities may enable attackers to access sensitive information and inject harmful scripts directly into a site’s backend, compelling site administrators to conduct urgent WordPress security assessments and potential malware eradication.
Gootloader exploits these WordPress security weaknesses in an especially nefarious manner through SEO poisoning. This strategy entails utilizing compromised WordPress sites to achieve high rankings in search engine results for specific queries, often related to legal documents, business contracts, and similar subjects that are likely to attract professional users. Upon visiting one of these compromised pages, malicious scripts present on the site prompt users to download a “necessary” document, which is, in reality, the Gootloader payload. By focusing on high-ranking WordPress pages in specialized domains, Gootloader effectively capitalizes on the trust users place in search engine results and the reputation of WordPress, while potentially delivering a destructive malware payload into corporate networks.
Moreover, the intuitive interface of WordPress, designed to minimize challenges for non-technical administrators, can unintentionally create vulnerabilities for malicious actors. Default configurations, when inadequately adjusted, may leave websites susceptible to attacks. For example, a significant number of WordPress administrators neglect to deactivate XML-RPC, a feature facilitating remote interactions with the site that can be leveraged for brute-force assaults. By exploiting these vulnerabilities, Gootloader identifies convenient access points to launch attacks, disseminate malware, and ultimately compromise secure networks.
How Gootloader Functions: From SEO Manipulation To Payload Delivery
Gootloader's attack methodology initiates with SEO manipulation—a strategy that alters search engine results to entice users into accessing maliciously compromised sites, particularly those involving vulnerable WordPress installations. This approach is fundamental to Gootloader's dissemination strategy, specifically focusing on high-ranking keywords associated with professional inquiries (such as “business contract template”) that attract organic traffic. Cybercriminals exploit compromised WordPress sites to achieve elevated rankings in search results, ensuring that unsuspecting users, frequently IT experts or corporate staff, come across these sites during standard search activities.
Upon a user arriving at one of these compromised domains, Gootloader employs sophisticated JavaScript injection techniques to assess whether the visitor satisfies certain criteria before commencing the attack. This targeting generally entails evaluating the user's geographic location, IP address, and referrer to verify their entry through a search engine result, thereby enhancing the likelihood that the visitor is legitimate. If these criteria are fulfilled, the malware dynamically incorporates a fraudulent document download link into the page, often formatted as a PDF or DOC file, crafted to mimic the authentic document the user was seeking.
This progression from mere SEO manipulation to payload execution relies on a combination of HTTP requests and PHP-based server-side scripts. When the user clicks on the link to obtain what they perceive as a valid document, they inadvertently receive the initial malware payload, commonly concealed within a ZIP or JavaScript file. This downloaded file contains code intended for PowerShell or JavaScript execution that activates the Gootloader payload within the victim’s environment, effectively circumventing most endpoint security measures by masquerading as a “safe” download.
Payload Configuration and Command-and-Control (C2) Interaction
Once integrated into the target environment, Gootloader transitions from infiltration to sustained command-and-control (C2) interaction and lateral mobility. The payload of the malware is structured in a modular way, facilitating attackers to change and implement a range of malware iterations depending on their objectives, which encompass ransomware, spyware, and data exfiltration approaches. This modular design affords attackers the adaptability to customize the infection to target specific high-value entities or sensitive settings.
Gootloader's C2 framework heavily depends on encrypted communication pathways to elude detection by conventional network surveillance systems. The payload, which frequently incorporates PowerShell and JavaScript scripts, initiates encrypted HTTP POST requests to pre-defined C2 servers. These servers relay directives back to the malware, allowing it to download supplementary payloads, execute additional commands, or transmit compromised data.
Within this framework, Gootloader utilizes intricate encoding methodologies to obfuscate its communications, complicating the task of security solutions to recognize malicious traffic. PowerShell, for example, serves as a crucial element for these operations, providing powerful scripting functionalities that are often whitelisted or overlooked in enterprise environments. JavaScript, on the other hand, plays an essential role in sustaining ongoing communication with the C2 servers and executing commands as required. By integrating these programming languages within the attack sequence, Gootloader guarantees flexibility and adaptability—both vital for malware-targeting security-enhanced environments.
A particularly significant advancement in Gootloader’s toolkit is the recent integration of GootBot, which augments the malware’s capabilities for executing lateral movement within corporate networks. GootBot permits Gootloader to extend its operations beyond initial infection vectors, thereby identifying and infiltrating additional systems throughout the network. By employing lateral movement techniques such as leveraging Windows Management Instrumentation (WMI) and Remote Desktop Protocol (RDP)—GootBot can broaden its influence, heightening the overall consequences and complicating the removal of WordPress malware once an infection has established itself. This strategy further empowers Gootloader to deploy ransomware or other supplementary payloads on a more extensive scale, magnifying its threat level.
Understanding The Security Implications
The Gootloader attack sequence illustrates the extent of vulnerability that sites and networks face when preventive strategies are overlooked. Mitigating the vulnerabilities that Gootloader exploits necessitates the implementation of proactive defenses across multiple layers, commencing with the fortification of WordPress sites. Regularly updating plugins, themes, and the foundational WordPress framework is critical for reducing security exposures. Nonetheless, given Gootloader’s multi-vector methodology, supplementary measures such as file integrity monitoring, HTTP request logging, and JavaScript behavioral analysis become essential for identifying early signs of SEO poisoning and payload insertion.
Moreover, instituting comprehensive C2 detection protocols and encrypting network communications are imperative defenses against the encrypted C2 channels utilized by Gootloader. Vigilantly monitoring for anomalous traffic patterns such as surges in POST requests or atypical PowerShell activity can act as preliminary indicators of potential C2 communications. For websites and systems under Gootloader’s threat, the deployment of advanced logging solutions and network analysis tools can enhance visibility into these patterns, facilitating both early detection and expedited remediation.
Secure Your WordPress Site Against Gootloader With Bluella
Bluella emphasizes an all-encompassing approach that integrates regular security assessments, stringent access controls, and continuous monitoring to thwart potential breaches. These are our methodologies specifically designed for WordPress security that can shield your site from Gootloader and other advanced malware threats.
i. Regular Audits and Vulnerability Scans
Consistent security assessments are crucial for identifying vulnerabilities prior to exploitation. Bluella conducts an in-depth analysis of potential WordPress security threats and is exceptionally efficient in malware detection and firewall defense. Our Threat Defense Feed continuously updates malware signatures, facilitating the identification of emerging threats such as Gootloader. We also provide functionalities such as server-side scans that can detect unauthorized changes and malware signatures within core files, themes, and plugins.
Establishing automated scans simplifies vulnerability management by ensuring issues are promptly flagged and documented. For optimal outcomes, schedule automated scans during peak traffic periods to identify active threats in real time. The process of WordPress malware eradication becomes more efficient when accompanied by consistent logs and alerts that pinpoint and isolate suspicious activities at an early stage, thereby minimizing the necessity for urgent remediation.
ii. Securing Plugins and Themes: Update and Hardening Protocols
Within the WordPress ecosystem, plugins and themes frequently represent the initial vulnerability points. Limiting the functionality of plugins is critical; for example, deactivate any plugin that possesses redundant features, which could expand your attack surface. Moreover, regular updates are indispensable. Trustworthy plugins and themes, those supported by active development teams receive frequent updates, addressing security vulnerabilities as they arise.
The hardening of plugins and themes extends beyond mere updates. Strategies such as deactivating XML-RPC diminish brute-force attack vectors. XML-RPC, a legacy feature of WordPress, permits external applications to interface with the site but is often misused by attackers for unauthorized logins and DDoS attacks. It is recommended to implement least privilege permissions to strictly limit plugin access to only those necessary for designated functionalities, thereby reducing risk in the event of a compromise.
iii. Enhanced Authentication and Access Management
Considering Gootloader’s capability to breach through weak login credentials, effective access management is crucial. By integrating multi-factor authentication (MFA), WordPress sites can notably improve their security through an extra user verification layer. Various WordPress plugins, including Duo Two-Factor and Google Authenticator, facilitate MFA, ensuring that even if credentials are compromised, unauthorized access remains exceedingly difficult.
Robust password policies serve as another essential line of defense. Enforce complex, non-reusable passwords and apply IP filtering to restrict access to the admin panel. By confining access to particular IP addresses or ranges, you can confirm that only authorized users can log in. Furthermore, incorporating CAPTCHAs on login pages acts as a deterrent to automated bots, thereby diminishing brute-force attack risks and bolstering WordPress website security by filtering out malicious login attempts.
iv. Deploying WAFs and Advanced Security Plugins

A Web Application Firewall (WAF) serves as an essential safeguard by scrutinizing and regulating HTTP traffic flowing between the internet and your website. WAF solutions like Cloudflare and AWS WAF provide customizable configurations to obstruct harmful IPs, filter SQL injection attempts, and mitigate DDoS attacks. By intercepting malicious traffic prior to its arrival at the server, WAFs demonstrate high efficacy against various cyber threats, including those orchestrated by malware such as Gootloader.
Advanced security plugins, including iThemes Security Pro, enhance WAF capabilities by introducing additional security layers within the WordPress environment. iThemes incorporates features such as brute force protection, bot detection, and database safeguarding, among others. Equipped with functionalities to monitor login activities, disable PHP file execution in designated WordPress directories, and enforce security logging, it provides site administrators with robust tools to counteract Gootloader and similar malware. These plugins significantly enhance the effectiveness of regular WordPress security assessments by maintaining comprehensive records of blocked IPs, detected code injections, and database changes.
v. Code Integrity and File Monitoring Techniques
To identify malicious code injections and unauthorized file alterations, it is imperative to deploy file integrity monitoring solutions. Instruments such as Wordfence’s File Integrity Scanning and WP Activity Log assist in tracking any anomalous modifications within core files, themes, or plugins. These tools generate detailed logs and reports that facilitate the early detection of code changes—an essential measure when confronting a threat like Gootloader, which frequently employs encoded payloads for evasion.
It is advisable to establish server-side monitoring to oversee system logs for unauthorized commands or irregular file alterations, particularly within critical WordPress directories. Code integrity tools are designed to detect discrepancies in core file structures, alerting administrators when files are unexpectedly modified, added, or removed. Promptly identifying these changes is vital for swift WordPress malware eradication, as it hinders malware from infiltrating deeper into your system.
Bluella's Enhanced Security Configurations for High-Security WordPress Websites
i. Restricting Server Permissions and Configurations
File permissions are frequently underestimated yet are vital for strengthening WordPress security through the limitation of access to files and directories. In the standard setup, files are expected to be allocated permissions of 644, ensuring the owner has the ability to read and write, while other users can only read, and directories are meant to have permissions of 755, granting the owner full access and others limited to read and execute. This setup effectively prevents unauthorized modifications to critical files, thereby mitigating the risk of illicit script executions that could result in vulnerabilities such as cross-site scripting (XSS) or SQL injection.
An additional essential recommendation is to disable PHP execution in non-critical directories. PHP files within the /wp-content/uploads and /wp-includes folders, for example, are common targets for cybercriminals aiming to execute harmful scripts. Disabling PHP execution in these folders by creating a .htaccess file with the specified rule can markedly improve security:
apache

This measure ensures that no PHP file can be executed from these directories, thereby minimizing the potential vulnerabilities for malicious scripts.
ii. Utilizing HTTPS and Security Headers for Improved Security
For WordPress installations that manage sensitive information, mandating HTTPS with SSL/TLS certificates is crucial. An SSL certificate safeguards data during transmission, shielding it from interception or alteration by unauthorized entities. Nevertheless, merely adopting HTTPS is insufficient. HTTP Strict Transport Security (HSTS) headers mandate that all subsequent connections to your website occur over HTTPS, regardless of whether a user initially attempts to connect via HTTP. To enforce HSTS, incorporate the following header in your server configuration:
apache
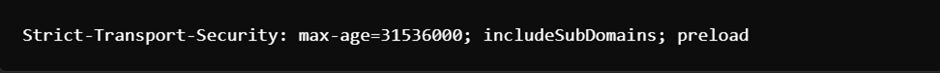
The max-age directive defines the duration for which the browser is mandated to apply HTTPS for your domain, whereas includeSubDomains broadens the enforcement to encompass all associated subdomains. This header not only safeguards data during transmission but also mitigates the risk of SSL stripping attacks, in which adversaries downgrade secure HTTPS requests to standard HTTP.
In addition, utilizing security headers such as Content Security Policy (CSP) and X-Content-Type-Options creates an effective barrier against XSS and numerous injection-related threats. CSP constrains the resources that the browser is permitted to load, thereby limiting JavaScript execution to only those sources that have been deemed trustworthy. A sample CSP header could be illustrated as follows:
apache
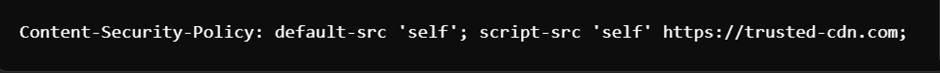
This policy ensures that only scripts that are sourced from your specified domain or a validated CDN are authorized to execute, thus significantly reducing the risk of malicious JavaScript injection. Likewise, configuring the X-Content-Type-Options header to nosniff inhibits browsers from misinterpreting files as a different MIME type than what is declared, thereby safeguarding against specific forms of injection attacks.
iii. Utilizing CDN for Enhanced Security and Scalability
A Content Delivery Network (CDN) is frequently linked with optimizing website performance by caching content on globally distributed servers, which diminishes load times for end-users. However, modern CDNs also deliver comprehensive security functionalities that can bolster the security posture of WordPress websites. CDNs provide an additional protective layer by screening out harmful traffic prior to its arrival at your site's origin server. This screening mechanism encompasses defenses against DDoS attacks, automated bot traffic, and SQL injection threats.
CDNs additionally facilitate SSL offloading, wherein SSL/TLS encryption and decryption processes are conducted by the CDN instead of the origin server, alleviating the load on your server and enabling it to accommodate a greater volume of legitimate traffic. Furthermore, the majority of CDNs incorporate a WAF that continuously scrutinizes HTTP requests for indicators of malicious behavior, obstructing traffic that displays characteristics typical of attacks.
For enhanced specificity in security management, numerous CDNs provide customizable rule configurations that empower you to establish precise security parameters for your WordPress site. For instance, if certain ranges of IP addresses are marked as potentially risky, one can establish rules to automatically block requests from these IPs, consequently boosting the security of your WordPress site with minimal hands-on effort.
Are you constantly battling malware threats on your WordPress site, concerned that your current security setup isn’t enough to stop sophisticated attacks?
At Bluella , we recognize the dynamic nature of online threats and the specific vulnerabilities that high-security WordPress platforms encounter. Our customized solutions extend beyond fundamental security protocols to establish multi-tiered defenses that proactively thwart breaches prior to their occurrence. From sophisticated configuration management to continuous monitoring, we tackle each vulnerability point to fortify your website against even the most tenacious malware threats. Allow us to manage your security concerns so you can concentrate on expanding your business with assurance.
Contact us today to discuss a tailored solution for your requirements.



