The expansion of digital connectivity presents unparalleled opportunities for small and emerging enterprises; however, it simultaneously introduces a growing spectrum of cyber threats. To maintain competitiveness and ensure security, organizations must remain informed about cybersecurity trends and strategies that can effectively mitigate risks.
1. The Emergence of Zero Trust Architecture
The Zero Trust framework, grounded in the notion of “never trust, always verify,” has become fundamental to contemporary cybersecurity practices. In stark contrast to conventional security paradigms that depended on perimeter defenses, Zero Trust regards every entity, whether internal or external to the organization’s network, as a potential risk. This paradigm has gained momentum recently and is increasingly essential for enterprises seeking to protect sensitive information.
Recent statistics indicate that over 40% of organizations globally are projected to implement some variant of Zero Trust architecture by the conclusion of 2024. This escalation underscores the critical role of identity and access management (IAM), multifactor authentication (MFA), and least-privilege principles within the current corporate landscape. Organizations, irrespective of their scale, can utilize Zero Trust to thwart unauthorized access by continuously monitoring user activities and validating identities prior to granting resource access.
For expanding enterprises, embracing Zero Trust not only guards against unauthorized access but also enhances overall cybersecurity by instituting stringent controls over who can access particular data and applications.
2. Cloud Security: Focus on Fortifying Multi-Cloud Environments
As organizations progressively transition more of their operations to cloud infrastructures, multi-cloud strategies are becoming increasingly prevalent. Nonetheless, the use of multiple cloud platforms also amplifies security risks. Research indicates that approximately 81% of organizations currently depend on various cloud service providers, thereby complicating their security posture.
Misconfigurations in cloud security settings are a primary contributor to data breaches. For example, inadequately configured cloud storage can inadvertently expose confidential information to public access. This scenario can prove especially challenging for small and medium-sized businesses (SMBs) that may have limited cybersecurity expertise. In multi-cloud configurations, it is imperative to deploy robust data encryption, IAM protocols, and automated monitoring systems to detect anomalous activities across all utilized cloud platforms.
As multi-cloud environments become standard, organizations require comprehensive tools to enforce uniform security policies across diverse settings and to effectively tackle prevalent cloud vulnerabilities.
3. AI and Machine Learning In Cyber Defense
The deployment of artificial intelligence (AI) and machine learning (ML) is becoming increasingly prevalent for the detection and real-time response to cybersecurity threats. These advanced technologies possess the capability to process extensive datasets at unparalleled velocities, thereby assisting organizations in identifying and addressing anomalies indicative of potential security breaches.
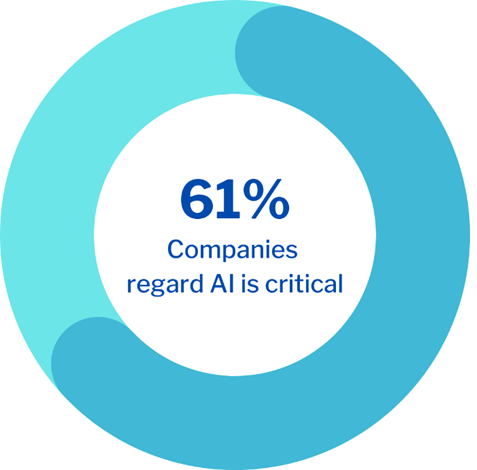
A recent analysis indicated that 61% of enterprises regard AI as a critical component of their cybersecurity strategies, with AI-enhanced solutions anticipated to detect threats more swiftly than traditional human-driven methods. By scrutinizing historical data, AI can also forecast probable attack patterns, facilitating proactive threat management.
For expanding organizations, the integration of AI-driven security solutions not only optimizes operational efficiency but also enhances scalability and predictive analytics. This paradigm shift fosters more flexible cybersecurity protocols, which are especially advantageous as companies grow. Utilizing AI and ML can significantly diminish detection intervals and bolster an organization’s capability to counteract threats, rendering it a prudent investment for enduring security.
4. Endpoint Security: Safeguarding Remote Work Devices
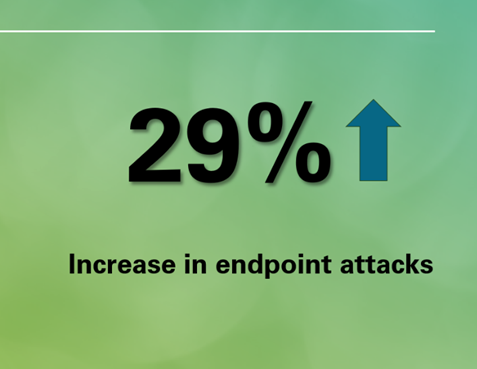
As remote work solidifies its presence in the corporate landscape, endpoint security has emerged as a pivotal concern. Each employee's device, whether a laptop, smartphone, or tablet—poses a potential vulnerability for cyber intrusions. A 2024 analysis revealed a 29% surge in endpoint attacks relative to prior years, emphasizing the critical necessity for robust security frameworks.
Endpoint security strategies, including device encryption, mobile device management (MDM), and remote oversight, are essential for ensuring the integrity of these remote devices, even when they operate beyond the corporate firewall. Nevertheless, many expanding enterprises neglect endpoint security, thereby jeopardizing their data and systems. The application of endpoint security technologies and methodologies, coupled with employee training on secure device practices, can effectively mitigate these vulnerabilities. As remote work persists, prioritizing endpoint security is imperative for organizations seeking to safeguard sensitive data and uphold secure communications.
5. Emphasis On Regulatory Compliance And Cyber Insurance
In light of the surge in data breaches, regulatory authorities are enacting more stringent cybersecurity compliance mandates, which influence how organizations manage personal and sensitive data. The General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) are now joined by fresh, sector-oriented directives around the globe, adding complexity to compliance efforts.

Additionally, cyber insurance is gaining momentum as organizations pursue coverage for losses associated with data breaches. Notably, the year 2024 has witnessed a 35% uptick in cyber insurance uptake among small and medium-sized businesses (SMBs), as organizations acknowledge the significance of financial protection in the wake of an attack. However, the process of securing cyber insurance is becoming progressively rigorous, with insurers mandating that businesses adhere to specific cybersecurity criteria to qualify for coverage. For developing organizations, prioritizing compliance not only mitigates legal liabilities but also fosters customer confidence. Furthermore, while cyber insurance offers a financial buffer, companies must uphold a robust security framework to qualify for such coverage.
Don’t let cyber threats hold back your growth, reach out to Bluella for a tailored cybersecurity strategy that aligns with your startup/company goals. Together, we can safeguard your digital assets and prepare your business for the future. Contact us today to get started!



