Network Function Virtualization (NFV) has revolutionized contemporary networking by substituting proprietary hardware-centric network devices with software-defined, virtualized functionalities. As NFV adoption accelerates, the intricacies of its security landscape also intensify. Achieving resilience in NFV extends beyond mere uptime; it encompasses the development of a secure, adaptive, and robust network capable of enduring evolving threats.
Shift From Hardware To Software-Defined Networks
The evolution from hardware-centric networking to software-defined architectures has fundamentally altered the methodologies companies employ to construct and administer networks. NFV separates network functionalities such as firewalls, load balancers, and routers from dedicated hardware, allowing them to operate as software on standard server infrastructure. This transition removes vendor lock-in, expedites service deployment, and lowers capital expenses. However, virtualization introduces a multilayered abstraction that intrinsically complicates security.
Increased Attack Surface Due To Virtualization
In conventional networks, security mechanisms are closely integrated with hardware, creating a relatively static and well-defined perimeter. NFV, on the other hand, functions within dynamic settings where virtual machines (VMs), containers, and APIs engage in continuous interaction. Each of these elements contributes to the attack surface:
- Hypervisors: Serving as the foundation of virtualization, a compromised hypervisor can provide attackers with control over all linked virtual machines. A report from VMware emphasizes that hypervisor attacks have surged by 35% over the last three years due to their pivotal function in network operations.
- APIs and Orchestration Tools: Open APIs utilized for VNF management often represent a vulnerability, as inadequate authentication or misconfigurations may expose sensitive processes to potential attackers.
- Data in Transit: Within virtualized networks, data traverses software-defined pathways, rendering encryption and secure tunneling critical yet frequently inconsistently executed.
Components Of NFV Architecture
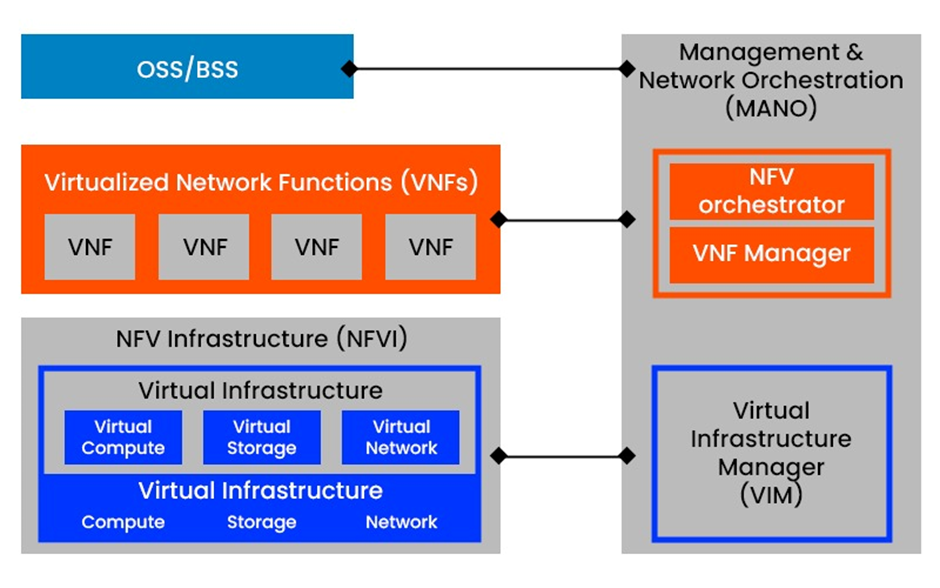
Virtual Infrastructure Layer Security: Protecting Hypervisors and VMs
At the core of Network Function Virtualization exists the virtual infrastructure, which encompasses hypervisors, virtual machines (VMs), and physical servers. Although these elements offer scalability and adaptability, they simultaneously create considerable attack vectors that necessitate stringent security protocols. The hypervisor, responsible for overseeing VMs, represents a particularly high-value target, as a single compromise can jeopardize all VMs operating on the system. Advanced malware such as Cloudburst has exposed weaknesses in hypervisors, capitalizing on vulnerabilities such as buffer overflows and privilege escalation. To counteract these threats, deploying fortified hypervisors with reduced attack surfaces is essential.
Providers like VMware and KVM now present enhanced security functionalities, including comprehensive patch management and runtime integrity monitoring. Periodic penetration testing further guarantees that vulnerabilities are detected and resolved in a timely manner. Alongside hypervisor defense, isolating VMs executing VNFs is crucial to avert lateral movement within the network. Secure boot protocols and encrypted storage defend VMs against unauthorized alterations and access. Lastly, ensuring comprehensive data security is of utmost importance. Encrypting VM snapshots and virtual disk files secure sensitive data from unauthorized exposure while safeguarding data in transit through protocols such as TLS and IPsec guarantees confidentiality and integrity across virtualized infrastructures.
VNF Layer Security: Securing Individual Network Functions
VNFs constitute the operational nucleus of NFV, performing essential roles such as firewalls, load balancing, and intrusion detection. However, their modular and adaptable characteristics also render them vulnerable to various security threats. VNFs acquired from external vendors must undergo rigorous code integrity assessments to uncover potential backdoors or malicious code embedded within them. Blockchain technology is progressively being harnessed to secure the unchangeable nature of VNF code and to verify its source, thus contributing an extra safety net.
Given that VNFs function in dynamic settings, runtime monitoring solutions such as Falco and Sysdig are vital for identifying anomalies, such as unauthorized processes or unusual network traffic patterns. Furthermore, maintaining VNFs with timely updates via automated patch management is critical for mitigating known vulnerabilities. Tools like Ansible facilitate this process, enabling efficient patch deployment while minimizing downtime and human errors, thereby ensuring the security and dependability of these essential network functions.
NFV Orchestration Layer Security: Protecting Orchestration Tools and APIs
The NFV Management and Orchestration (MANO) layer manages the lifecycle of VNFs, establishing it as a pivotal point for security considerations.
i. API Security:- APIs enable interactions among VNFs, orchestration tools, and the foundational infrastructure; however, inadequately secured APIs present a considerable threat. A Verizon Data Breach Investigations Report indicated that API vulnerabilities represented 35% of application-layer attacks in 2022.
- API gateways must implement rigorous authentication, rate limiting, and input validation to reduce exposure to risks.
- Adopting OAuth 2.0 and OpenID Connect for API authorization guarantees secure and precise access management.
ii. Access Control Policies: Role-based access control (RBAC) and multi-factor authentication (MFA) can restrict unauthorized entry to orchestration tools.
iii. Configuration Integrity Monitoring: Tools such as Tripwire can continuously monitor and notify for unauthorized alterations in orchestration configurations, thus aiding in preserving the integrity of NFV implementations.
Utilizing Zero Trust Architecture For NFV
The Zero Trust framework, characterized by “never trust, always verify,” aligns seamlessly with the requirements of NFV environments. By presuming that all entities, both internal and external to the network may pose potential threats, Zero Trust applies rigorous security protocols across all layers.
i. Implementing Least Privilege Principles
- Granular Access Controls: Limit access to VNFs and orchestration tools according to the minimum permissions necessary for operation. For instance, a VNF developer should not possess access to the administrative functions of the orchestration layer.
- Identity-based Policies: Employ identity-centric frameworks such as Azure AD Conditional Access to ensure that only authenticated and authorized users or devices can engage with NFV components.
- Audit and Review: Conduct regular assessments of access logs to pinpoint and retract unnecessary permissions. Solutions like Splunk can facilitate this process and identify suspicious activities.
ii. Role of Micro-segmentation in Isolating VNFs
Micro-segmentation establishes discrete zones within the NFV infrastructure, ensuring that threats cannot propagate laterally throughout the network.
- Dynamic Security Policies: In contrast to conventional segmentation, which depends on IP-based rules, micro-segmentation in NFV utilizes dynamic attributes such as VNF identity, application type, or workload sensitivity. This enables highly detailed and adaptive security controls.
- Integration with Software-defined Networking (SDN): SDN controllers like OpenDaylight can enforce micro-segmentation policies at the network level, dynamically adjusting to variations in VNF deployment or traffic patterns.
- Preventing East-West Attacks: By segregating VNFs from one another, micro-segmentation prevents attackers from moving laterally within the network, thereby limiting the potential impact of any breach.
Strategies For Developing Resilient NFV Networks
Building a resilient NFV network is essential in today's rapidly evolving and interconnected digital ecosystem. As organizations transition towards software-defined networking, maintaining robust security and seamless functionality across NFV environments has emerged as a fundamental element of IT strategies.
i. Secure Onboarding of VNFs
A critical initial step in creating a resilient NFV network is securing the onboarding procedure for VNFs. Given the dependence on third-party VNFs for operational flexibility, one must perform thorough assessments of these components. Industry best practices advocate for a rigorous analysis of VNF source code to uncover vulnerabilities or malicious backdoors. Research states that approximately 80% of cybersecurity incidents in NFV systems stem from compromised VNFs provided by external vendors.
Digital certificates and secure code signing serve as essential instruments for this objective. Certificates authenticate the origin of VNFs, ensuring they originate from reliable sources, while secure code signing utilizes cryptographic methods to validate the integrity of software packages. These practices prevent unauthorized alterations and enhance trust within the NFV architecture. Emerging technologies such as blockchain are also gaining popularity in this area, providing immutable ledgers to monitor VNF origins and modifications throughout their lifecycle.
ii. Encryption and Data Protection Across NFV Layers
Data security remains an indispensable element of resilient NFV networks, particularly at a time when network function virtualization supports critical infrastructures like IoT. As NFV layers enable extensive data exchanges, encrypting information at every interaction point is crucial to mitigate unauthorized access and data breaches.
Data at rest—such as VM snapshots and virtual disk files must be encrypted using robust algorithms like AES-256. Likewise, data in transit necessitates protection through advanced protocols such as TLS and IPSec. These measures are particularly vital for NFV networks integrated with IoT systems, where unsecured endpoints can represent vulnerabilities. Secure VPNs also play a significant role in encrypting communication pathways, ensuring end-to-end confidentiality.
Industry analyses emphasize that encryption decreases the probability of data breaches by more than 45%, rendering it an essential practice for NFV security. Furthermore, by utilizing centralized key management systems, your teams can effectively manage encryption policies across varied NFV environments.
iii. Monitoring and Threat Detection in NFV Systems
Real-time monitoring is a fundamental component of resilient NFV networks, enabling the early detection of anomalies that could escalate into significant cyberattacks. VNFs, characterized by their modular and dynamic nature, require continuous surveillance to identify indications of abnormal activity, such as unexpected increases in resource usage or unauthorized process executions.
AI-driven analytics have surfaced as formidable assets in this area. By examining extensive volumes of telemetry data, tools like Splunk and IBM QRadar can identify irregularities that conventional methods may overlook. For example, AI models trained on network baselines can highlight deviations in VNF communication patterns, facilitating proactive mitigation.
iv. Automation and Security in NFV
The advent of automation has transformed NFV architecture by optimizing workflows and minimizing human error, a frequent vulnerability associated with manual configurations. Utilizing AI and machine learning for automated threat mitigation can substantially enhance network resilience. For example, automated systems are capable of isolating compromised VNFs, rerouting traffic, and applying patches instantaneously without the need for human intervention.
The incorporation of SecOps into the NFV lifecycle strengthens the security framework. This methodology integrates security considerations into each stage of NFV deployment, from initial design through to decommissioning. SecOps tools are capable of automating compliance assessments, enforcing policy configurations, and dynamically responding to emerging threats.
Moreover, the implementation of micro-segmentation within NFV networks ensures that VNFs are compartmentalized, thereby reducing lateral movement in the case of a security breach. The Zero Trust Architecture principle enhances this by necessitating ongoing validation for resource access, which is a crucial strategy for NFV environments operating in critical sectors such as finance and healthcare.
Key Technologies Enhancing NFV Security
With essential infrastructures like IoT heavily dependent on NFV networks, employing cutting-edge technologies is vital to defend against advancing threats. Two notable technologies, containers and blockchain are rising as key elements of a fortified NFV security framework. By improving the agility, integrity, and scalability of virtual network functions (VNFs), these technologies are transforming the NFV security domain.
i. Role of Containers in NFV Security
In NFV architecture, the selection between virtual machines (VMs) and containers for hosting VNFs critically influences the security stance of a network. While VM-centric VNFs have historically prevailed, containers are increasingly favored due to their lightweight characteristics and operational effectiveness. Nonetheless, this transition necessitates a thorough analysis of security implications.
ii. Comparison of VM-based and Containerized VNFs
VM-based VNFs inherently provide strong isolation, as each VM operates with a complete operating system and its own kernel. This design inherently enhances security against lateral attacks; a breach in one VM does not readily compromise others on the same physical host. However, this advantage is counterbalanced by increased resource consumption and extended deployment durations.
Conversely, containers utilize the host OS kernel, facilitating rapid deployment and optimized resource efficiency. This efficiency is essential for NFV networks integrated with IoT systems, where immediate responsiveness is critical. However, the shared kernel also expands the attack surface. A security flaw in the host OS or container runtime, such as those exploited in the Dirty Pipe vulnerability (CVE-2022-0847), could potentially jeopardize all containers operating on that host.
iii. Secure Container Orchestration with Kubernetes:
To alleviate these risks, container orchestration platforms like Kubernetes are essential. Kubernetes implements security best practices such as:
- Pod Security Policies: Enforcing detailed controls over container privileges and access rights.
- Runtime Security: Solutions like Falco can scrutinize containers for unauthorized activities.
- Network Segmentation: Kubernetes network policies facilitate precise control over inter-container communications, minimizing lateral movement in the event of a security breach.
Furthermore, utilizing features like Kubernetes Secrets for the secure management of sensitive information (e.g., encryption keys) and deploying mutual TLS for safeguarding API communications significantly enhances the security of containerized NFV implementations.
iv. Blockchain For VNF Integrity Assurance
Given that VNFs are procured from a variety of vendors, maintaining their integrity throughout their operational lifecycle presents a formidable challenge. The utilization of blockchain technology, characterized by its fundamental immutability and decentralized architecture, provides an effective mechanism for safeguarding VNFs from tampering and threats originating from the supply chain.
- Immutable Records of VNF Changes : Blockchain establishes a clear, tamper-resistant ledger documenting all activities associated with VNFs, encompassing deployment, modifications, and configurations. This makes sure that any unauthorized alterations are swiftly identifiable. For example, a permissioned blockchain network can chronicle alterations to VNF code, delivering cryptographic validation of authenticity and traceability. Such a methodology is especially pertinent in supply chain scenarios, where third-party VNFs may be susceptible to vulnerabilities or concealed backdoors.
- Preventing Supply Chain Attacks : Supply chain attacks, exemplified by the notorious SolarWinds incident, underscore the necessity for stringent mechanisms to validate software integrity. Blockchain facilitates the verification that every VNF incorporated into an NFV network is authenticated and devoid of tampering. By embedding blockchain within the NFV security framework, IT teams can create a reliable source of truth for VNFs, thereby diminishing the risk of compromised software penetrating the network.
- Applications in NFV and IoT : Within NFV networks that are integrated with IoT, wherein VNFs are required to handle sensitive data from distributed endpoints, blockchain introduces an additional layer of trust. It ensures that the data managed by VNFs remains secure and subject to audit. For instance, smart contracts can streamline compliance verifications, ensuring that VNFs conform to security protocols prior to their deployment or updates.
With the swift advancement of virtualization technologies and the growing dependence on NFV for scalable networking solutions, the imperative for robust security has escalated significantly. As a reputable collaborator in networking technology, Bluella provides comprehensive solutions that encompass every aspect of NFV security.
Why Bluella Is Your Optimal Partner For NFV Security
i. End-to-End Expertise in NFV Security Architecture : We excel in deploying multi-layered NFV security frameworks that safeguard the virtual infrastructure, VNFs, and orchestration layers. Our specialists utilize state-of-the-art tools to mitigate vulnerabilities across:
- Hypervisors and VMs: Deploying fortified hypervisors and sophisticated encryption methodologies to secure virtualized environments.
- VNFs: Performing extensive code integrity assessments and continuous runtime security surveillance to thwart exploitation attempts.
- Orchestration Layers: Protecting APIs and management frameworks through advanced encryption, RBAC (Role-Based Access Control), and ongoing monitoring.
ii. Containerized VNFs for Enhanced Security : As the sector shifts towards containerized VNFs for improved scalability and efficacy, Bluella makes sure the security of your Kubernetes-based orchestration frameworks:
- Pod Security Policies to mandate least privilege access.
- Network segmentation to compartmentalize workloads and inhibit lateral movement.
- Runtime monitoring solutions to identify anomalous activities in real time.
iii. Blockchain Solutions for VNF Integrity Assurance : We incorporate blockchain technology to bolster the integrity and traceability of VNFs. With our offerings, you can:
- Maintain immutable records of VNF deployments and updates, assuring tamper-proof operations.
- Mitigate supply chain attacks by verifying third-party VNFs with cryptographic certainty.
- Automate compliance assessments with smart contracts, ensuring VNFs conform to established security protocols prior to deployment.
iv. AI-Driven Threat Detection and Automation: Our solutions harness AI and machine learning to deliver real-time analytics and automated threat responses. This encompasses:
- Proactive identification of anomalies in VNF behavior.
- Automated patch deployment utilizing tools to ensure continuous protection.
- Integration of SecOps principles into the NFV lifecycle, seamlessly aligning security and operations.
Tailored Solutions For IoT-Integrated NFV Networks
IoT ecosystems facilitate exceptional connectivity, yet simultaneously render NFV networks susceptible to vulnerabilities across numerous endpoints. The presence of distributed devices results in elevated traffic volumes, thereby creating increased opportunities for data breaches and endpoint infiltrations. Bluella addresses these issues directly by crafting bespoke NFV architectures that integrate flawlessly with IoT systems while enhancing their security posture.
Our solutions emphasize endpoint security through advanced authentication mechanisms, encrypted communication channels, and dynamic workload segregation to minimize attack vectors. Regardless of whether you are overseeing hundreds or thousands of devices, we ensure that your NFV infrastructure functions at optimal efficiency without sacrificing security. By utilizing real-time analytics and predictive threat detection, we empower your IoT-integrated NFV networks to manage traffic spikes securely and effectively.
Compliance and Certification
Bluella assists you in navigating this intricate landscape by ensuring that your NFV deployments comply with standards such as ISO 27001 and GDPR.
Our compliance-centric approach entails integrating data protection strategies at every tier of your NFV network. From safeguarding virtual machines to encrypting sensitive information, we embed compliance as a fundamental characteristic of your architecture, not merely an afterthought. With Bluella, you can assuredly meet both existing regulations and future requirements, confident in the knowledge that your systems are audit-ready and resilient.
Partner with Bluella to transform your challenges into opportunities and redefine how your network operates. Let’s secure the future of your NFV network together— contact us today to learn more!



